This post was republished with permission from Zero Hedge
Most people are guilty of using a weak password at some point. But just how predictable can they be?
This infographic, via Visual Capitalist’s Marcus Lu, reveals the top 25 most commonly used passwords globally, from ‘123456’ to ‘password’.

The data for this visualization comes from NordPass, which analyzed the most frequently used passwords based on a 2.5TB database of credentials exposed by data breaches.
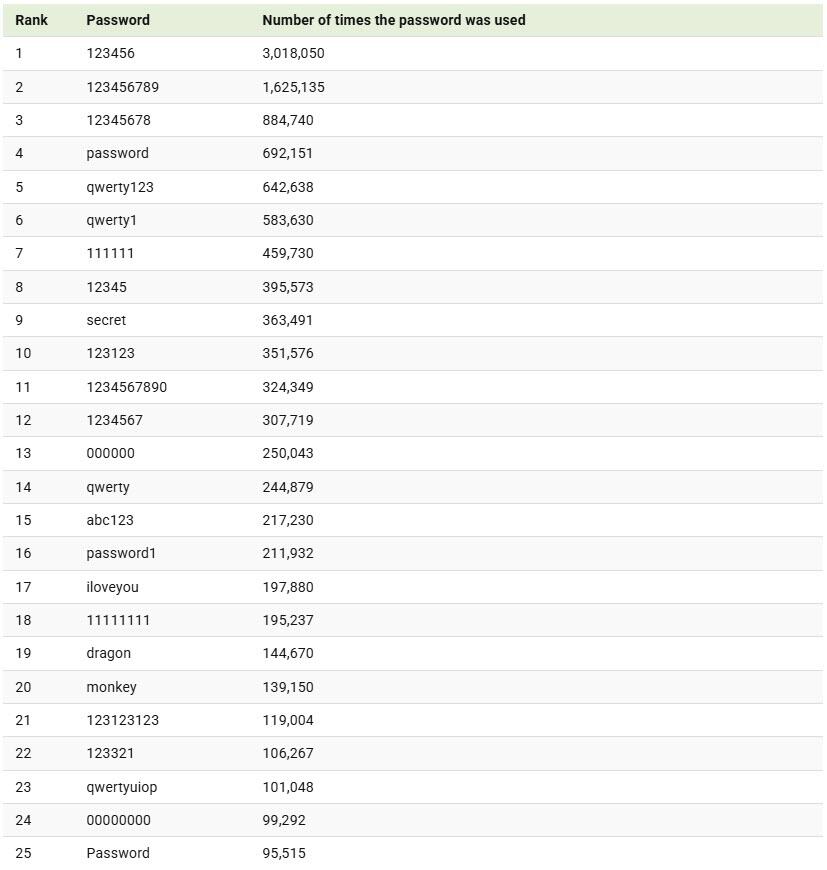
The top password—“123456”—was used over 3 million times in the dataset analyzed by NordPass. In fact, six of the top 10 passwords are purely numeric, highlighting how common predictable number patterns remain.
These types of passwords are among the easiest for hackers to guess using brute-force attacks, taking a matter of seconds.
Keyboard Patterns and Simple Words
Along with numbers, users often rely on keyboard sequences like “qwerty” or common words like “password” and “secret.” While these may be easy to remember, they’re also easy to hack. Variations like “Password” or “password1” offer little improvement in security.
How to Create a Strong Password
According to NordPass, your password should be at least 20 characters long and include uppercase and lowercase letters, numbers, and special symbols (e.g. @#$%). Some browsers, such as Google Chrome, can also suggest a strong password for you.
Additionally, NordPass suggests that you never reuse passwords. If one account were to be compromised, other accounts that share the same password could also be at risk.
If you enjoyed today’s post, check out The Five Most Common Cybersecurity Mistakes on Voronoi, the new app from Visual Capitalist.
Your support is crucial in helping us defeat mass censorship. Please consider donating via Locals or check out our unique merch. Follow us on X @ModernityNews.
More news on our radar
















“123456” was the factory password for the election server in Georgia. The terminal was in a hidden, unlocked room. After they tested the software and wireless connectivity to public terminals state wide they never changed the password.
If a machine broke down a rep from his or her polling station could call the server administrator that used the factory password to correct the problem remotely. Many states used the same technique or simply distributed passwords via unsecured channels.
Colorado posted the passwords on an unsecured website accessible by the public. A 10 year old could change the outcome of the 2020 presidential election to start WWW3. Mushroom clouds are cool.